The Misuse of the Use-Cases of CyberFactory#1
A Misuse-Case (MUC), which is derived from a Use-Case (UC)*, describes the steps and scenarios, which a user/actor performs in order to accomplish a malicious act against a system or business process. They are still UCs in the sense that they define the steps that a user performs to achieve a goal, even if the goal is not a positive or a desired one from the perspective of the business process or system designers.
A MUC covers for example:
- Safety hazards, irrespective of originating from security vulnerabilities or inherent to the novel technologies developed in the project,
- Security attacks by outsiders,
- Workers attacks,
- Insider threats will also be considered in the MUCs, giving the required attention to economical, psychological and societal aspects.
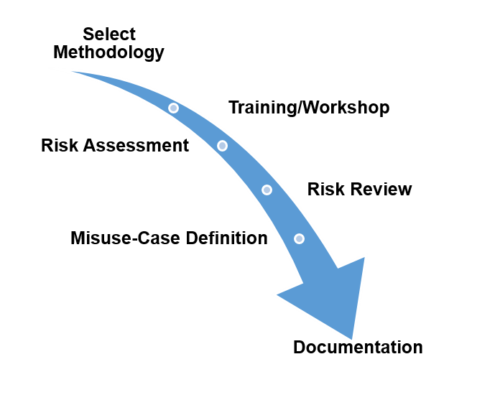 Figure 1: Misuse-Case Task Approach
Figure 1: Misuse-Case Task Approach
To be able to document the right MUCs, the project team first worked on selecting the appropriate approach. In the specific case of CyberFactory#1 (CF#1) it was decided that a two-phased approach was the preferred approach: first there was a collecting of generic and independent risks, which were then consolidated into MUCs.
Within CF#1 the risk assessment considered the following aspects
- Impact Level (categorized in high, medium, low)
- Probability Level (categorized in high, medium, low)
- Risk Source, Risk Source Type and Risk Location
- Attack Vector
- Vulnerability
- Target Asset and Target Asset Type
- Threat Agent and Threat Agent Type
- If applicable: References (CVE, etc.)
- Risk Result (Impact Detail), Outcome and Impact Nature
Example risk “Lack of OT capacity in current IT cybersecurity products (mainly SIEM)”
- High
- Medium
- SIEM & other IT based cybersecurity products | Legacy Infrastructure | FoF
- Technical security attacks against OT solutions
- Lack of OT interoperability for existing IT based SIEMs and existing cybersecurity products
- OT Systems | FoF
- Hackers & hacking software | Hacker
- N/A
- Stop of production | loss of safety
After the first stage, a total of 153 risks have been determined. Here are the statistics of those risks by their level and source type:
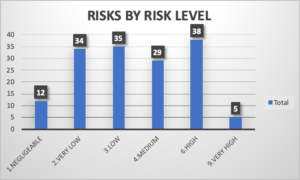
Figure 2: Risks by Risk Level
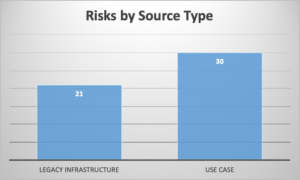
Figure 3: Risks by Source Type
As per the selected methodology and the risks, one (or more) misuse-cases were selected and defined further for each use-case within Cyberfactory#1 project. In particular, these risks were connected to the use-cases and their implementation with no risk mitigation available yet. The risks are assessed and listed based of the source type although there are many risks related with the new use cases, legacy infrastructure has also quite number of new risks that will be addressed within the project.
What’s next?
As the project team progresses through the main work packages and tasks, we always have the misuse-cases in mind in order to test, implement, perform our designs and projects while preventing them as a by-product in the scope of a security-by-design approach.
Author: Murat Lostar, CEO & Founder, Lostar Inc.
*To learn more about our use-cases, see our article on it here



